News
Ransomware Attacks Rise Dramatically
Posted in: Blogs, cyberattack, cybersecurity, InfoSec, operational technology, phishing, phishing attacks, phishing emails, ransomware, Security - Jul 22, 2021Success breeds success, as they say. And the rich rewards being reaped by ransomware attacks have led to a surge in these incidents. According to the Cybersecurity Threatscape by Positive Technologies, ransomware is now used in 45% of all malware-related attacks against organizations.
Read more: How to Handle Security Incidents and Data Breaches
Hackers Target Industrial and Health Sectors
Cyberattacks grew by 51% last year compared to 2019, and their frequency continues to rise. That is an awful lot of potential ransom dollars.
Attacks are becoming more targeted, too. There was a 91% jump in cyberattacks on industrial companies and a 54% rise in malware-related attacks to industrial firms compared to 2019. Similarly, the number of attacks on medical institutions increased by 91% — making the health care sector the top target for ransomware attacks currently.
The number of attacks on medical institutions increased by 91% last year.
“Amid the COVID-19 pandemic and overloaded health systems worldwide, hackers added fuel to the fire by disrupting the availability of medical information systems with devastating consequences,” said Positive Technologies analyst Yana Yurakova.
“In 2020, the total damage caused by ransomware attacks against medical institutions in the U.S. was estimated to reach $20.8 billion.”
Cyberattacks Become Less Random
Phishing is aptly named. You send out malicious links and attachments posing as a trusted source in order to get some unfortunate person to click, and then introduce malware into the enterprise. Like fishing, you put the line into the water and see what kind of fish comes along.
Traditional phishing is all about volume. You blast out loads of emails and sometimes you get a bite. But those days are coming to an end. The bad guys have decided to skip the sardines and go after marlin. According to the report, 7 out of 10 attacks are now aimed against specific, high-potential targets.
Industrial organizations, hospitals, financial services firms, schools, and local government are all ripe for a malicious campaign. They either represent deep pockets, or provide a service that can’t be denied to its users for any length of time. As such, the most popular targets are:
- Government institutions (19%)
- Industrial companies (12%)
- Medical institutions (9%)
Digital Transformation Creates New Targets
The industrial category represents a fairly new phenomenon in cybercrime. With digital transformation becoming something of a watchword, those in industry have been merrily tearing down the barriers between their IT systems and the Operational Technology (OT) systems that sit on the shop floor or production line. The result is a spike in attacks on industrial targets, with the Colonial Pipeline hack being the most notable.
Even more recently, vulnerabilities were found to exist in widely used Siemens programmable logic controllers (PLCs). These devices are used in assembly lines, industrial processes, power generation, and other facets of industry.
Read more: You Really Can’t Do Enough Security Training
Part of the problem is inexperience. When hackers began to use viruses in the early days, it was relatively easy to infect a user. Over time, antivirus and other protections became more mature. And users started to learn better security practices.
In the world of OT, this is all new. Some systems date back decades, and security was the last thing on the minds of their developers. As soon as you web-enable or digitize these applications, systems, and devices, it’s a Pandora’s Box in reverse — Pandora has a good chance of breaching the enterprise.
Cybersecurity Must Evolve
The Positive Technologies report noted that industrial companies are being attacked by a number of different ransomware variants stemming from various criminal gangs. Some of them delete backup files before starting the encryption process. They can also stop industrial control systems in their tracks. Phishing frequency against industrial targets is also on the increase.
Dmitry Darensky, Head of Industrial Cybersecurity Practice at Positive Technologies, listed a variety of other breaches of industrial targets: water infrastructure breached in Israel, an Indian power outage due to a cyberattack, and companies such as Huber+Suhner and Honda being forced to halt operations because of breaches.
Penetration tests or threat modeling audits are not enough to provide a sufficient assessment of current risks.
He added that penetration tests or threat modeling audits are not enough to provide a sufficient assessment of current risks. Neither are conventional security assessments.
“To simulate an attack without affecting real-life systems, digital twins or a cyber-range can be used,” said Darensky. “A cyber-range provides a safe environment where experts can get the most comprehensive picture of whether certain risks can be triggered (for example, oil storage overflow), protection mechanisms will respond in time, and infosec teams will detect and stop an incident.”
The post Ransomware Attacks Rise Dramatically appeared first on CIO Insight.
top9 Key Considerations When Building a Global Data Science Team
Posted in: Blogs, Careers, Collaboration, data science, data science team, Hiring, hiring challenges, hiring decisions, hiring diversity, IT Management, Leadership, Workplace - Jul 21, 2021What considerations should be made when building a global data science team?
To help business owners make a better informed decision about building a global data science team, we asked CEOs and business professionals to share their best insights. From building agile teams to adding accountability through analytics, there are several things to consider when building a global data science team.
Read more: What Are CIOs Looking for in Current IT Grads?
Here are nine key considerations for building a global data science team.
- Turn to Executive Search Firms
- Build Agile Teams
- Know the Team’s Purpose
- Bridge the Technical and Business Sides
- Establish Clear Goals
- Add Accountability Through Analytics
- Create a Scalable Team
- Consider Cultural Nuances
- Recruit a Leader and Members From Within
Turn to Executive Search Firms
When building a team of people with specific skill sets in a specialized field, consider turning to an executive search firm to build your team.
When recruiting for a global data science team, find a search firm that specializes in the functions and sectors that you’re looking for that can help fill your personnel gap. A search firm has the ability to deliver a slate of candidates with the right mix of knowledge needed for a specialized team.
Jon Schneider, Recruiterie
Build Agile Teams
When building a global data science team, you should consider building agile teams. While it is important to have people who are specialists in certain areas, having agile teams with generalists or people who can function in multiple areas of your operations can reduce bottlenecks. Fewer bottlenecks can increase your overall team productivity.
Debra Hildebrand, Hildebrand Solutions, LLC
Know the Team’s Purpose
I think there are two main considerations to be made when building a global data science team:
- Ask yourself, “What is the strategic purpose of the data?” What are you trying to achieve through this data? Is it going to be used as a part of an algorithm? Is it going to be used to develop a new technology? Is it going to be used for statistical purposes? Is it going to be sold for marketing purposes?
- Build a team that is most capable of collecting, analyzing, and leveraging the data based on its strategic purpose. If the data is going to be used to build and develop new technology, build a team that’s suited for that purpose. If the data is going to be used for marketing, build a team that will be able to meet that purpose.
Phillip Lew, C9 Staff
Bridge the Technical and Business Sides
Data translators are a newer role, but an addition that should be seriously considered when forming a global data science team. Data engineers and scientists are responsible for maintaining data and creating algorithms.
However, data translators bridge the gap between the technical side of a data science team and its business application by producing solid, actionable business insights from that data.
Guy Katabi, Lightkey
Establish Clear Goals
When building a global data science team, taking a step back to envision and establish a strategy is essential. Even the best talent can stumble if clear goals and structure are lacking.
Consider how centralized the team will be, how many members are needed, and what strategy will guide operations. Details like these form the foundation of a collaborative and like-minded team. Make goals clear to the entire data team to avoid silos and foster cohesion.
Claire Routh, Markitors
Add Accountability Through Analytics
The NewVantage Partners Big Data and AI 2020 Survey reports that 26.8% of the participants had no accountability for the business intelligence insights being delivered. This may be closely related to the fact that 72.1% of the firms in the survey struggle with appointing a data science team leader.
We can all agree that investing in business performance analytics is valuable. With these tools, you can get full, clear, and real-time insights into your running processes and team performance. Together with investing in such a solution, take an additional step by establishing an accountable data science team leader.
Spiros Skolarikis, Comidor
Create a Scalable Team
You will find data science teams to be unique to each organization depending on their needs. However, when building a high-performing team, scalability matters. Part of achieving this is by ensuring that teams are cross-functional and value-driven.
Michael Thompson, Lurn Agile
Consider Cultural Nuances
When building a global data science team, it is important to consider cultural differences and norms. Many managers make the mistake of assuming that data is a universal language, and skip team building.
However, while team members may be working most directly with data, they also need to cooperate with each other. When building a global team, work styles can differ from country to country, region to region, or even location to location. When working remotely, teammates have fewer chances to interact and build a natural rapport.
Yet communicating and delegating are still essential to the team’s success, even if each group member has assigned duties. Managers should take time to introduce teammates, clarify roles, and foster camaraderie, even when the nature of the work is highly independent.
Michael Alexis, TeamBuilding
Recruit a Leader and Members From Within
One of the crucial aspects of having a powerful global data science team in your company is to load-balance the machine learning (ML) models throughout the business. Therefore, leading a team to deliver the needed data insights is on the team leader. Also, start the process by diving right into your executive team.
Be sure to check if any of your in-house employees have ever done any certifications on ML before you recruit any external talent. List current employees who can be efficiently trained to work within the data science team.
Eden Cheng, WeInvoice
Read next: HRIS Trends for 2021: The Future of HR Management
Terkel creates community-driven content featuring expert insights. Sign up at terkel.io to answer questions and get published.
The post 9 Key Considerations When Building a Global Data Science Team appeared first on CIO Insight.
topClosing the Governance Gap: Enabling Governed Self-Service Analytics
Posted in: Business Intelligence - Jul 15, 2021This webinar is a must for personnel with an analytics and technology mandate to learn about the root causes of this governance gap and consider ideas for closing the gap. top
How to Handle Security Incidents and Data Breaches
Posted in: Blogs, cyber-security, cybersecurity, cybersecurity best practices, detecting security incidents, IT Strategy, malware, News & Trends, Security, security incident and event management, security incident response, security incidents - Jul 14, 2021Security incidents and data breaches are on the rise.
The Verizon Data Breach Investigations Report (VDBIR) analyzed almost 80,000 security incidents around the world. More than 5,000 were classified as confirmed data breaches. About a third of the time, phishing is the attack vector that leads the attack. Next come web application attacks and system intrusions. An astounding 85% of breaches contain a human element, whether that is a user clicking on something malicious, compromised credentials, or an insider threat. Ransomware was present in about 13% of breaches.
Read more: 2021’s Most Successful Phishing Ploys (So Far)
Because your organization is so likely to be attacked, preparing a clear-cut security incident response plan is essential. So, what do you do if you suffer a security incident?
What Are Security Incidents?
First, you need to know what an incident is. The VDBIR defines an incident as a security event that compromises the integrity, confidentiality, or availability of an information asset. The report defines a breach as an incident that results in the confirmed disclosure of data to an unauthorized party.
Eleanor Barlow of SecurityHQ offered examples of security incidents such as:
- Unauthorized access to a system
- Attempts to gain unauthorized access
- Malicious disruption or denial of service
- Unauthorized use of systems
- Changes to firmware, hardware, or software without consent
- Accidental breaches, such as emails forwarded to the wrong recipients
Barlow stressed that speed is vital when it comes to breaches or security incident management. Do not waste time hoping the event won’t be serious, or attempting to cover it up. Disclose the incident rapidly, so action can be taken to limit the potential damage.
“The faster a breach is detected, the faster the response, the greater the chance systems and processes can be put in place to mitigate the consequences of the attack, or at least future attacks, and limit the cost and damage involved,” Barlow said.
Create a Security Incident Response Plan
As recently as 2016, 34% of responding U.S. IT professionals said C-level executives are never updated on security incidents. As such, your company may not be adequately prepared to face a breach. However, you can combat this problem by formulating a comprehensive response plan now.
According to Varonis, a data security and analytics company, there are six steps to creating an incident response plan:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
The first step to combating a security incident is preparing triage protocols. With those in place, your team can act quickly to identify and contain a threat once it appears. Only then can your organization eradicate the threat, recover salvageable data, and restore or rebuild compromised devices. The final step of your plan should be reviewing lessons learned, and implementing new measures to stop the next threat.
Review Varonis’ comprehensive guide for more details on developing a security incident response plan.
Preparing for Security Incidents Is Everyone’s Job
Preparing your organization to spot security incidents before they become breaches is key. This includes the workforce in general; prevention isn’t only up to IT or security threat analysts. When personnel know what to look for in terms of suspicious emails or links, the organization is alerted more rapidly — and your security incident plan is put into action faster.
Read more: You Really Can’t Do Enough Security Training
Take the case of someone in Finance falling for a phishing email. The person’s email account is compromised, and bad actors then use it to send phishing emails to others in the company. If personnel are not educated well, the infection will spread laterally from email account to email account, making it harder to stop. But if a vigilant employee flags the suspicious email to IT, then catastrophe can be averted.
Your organization needs to understand their legal obligations as well. Employees can be liable if they knowingly withhold knowledge of a data breach or security incident. Many industries must report breaches — and their extent — in a timely manner. Notably, FBI Director Christopher Wray recently compared the current ransomware threat to combating terrorism after September 11, 2001.
Because security incidents are so common, your best defense is preparation. Implement a security incident response plan and educate employees before your organization becomes the next Colonial Pipeline.
The post How to Handle Security Incidents and Data Breaches appeared first on CIO Insight.
topSage X3 ERP Software: The Pros & Cons for 2021
Posted in: Application Development, automation, Big Data, Business Intelligence, configuration management, customer support, Enterprise Apps, enterprise resource planning, Enterprise Resource Planning (ERP), ERP, IT Management, Project Management, quality control, Sage, Sage X3, Sage X3 ERP, scalability, UX/UI, Workplace - Jul 12, 2021Sage X3 is a top player in the enterprise resource planning (ERP) software market, particularly for businesses searching for a usable interface with strong functionality and integrations at a reasonable cost.
Like other ERP tools, Sage X3 makes it possible for businesses to combine software and operational needs, ranging from business intelligence (BI) to human resources to supply chain management to manufacturing management.
See below to learn about the pros and cons of Sage X3 and some other resources your team can use to guide their ERP selection process.
Learn About Current Trends in ERP: Three Key Advances in ERP for 2021
A Closer Look at Sage X3 ERP
The Pros of Sage X3 ERP
User-Friendly Interface
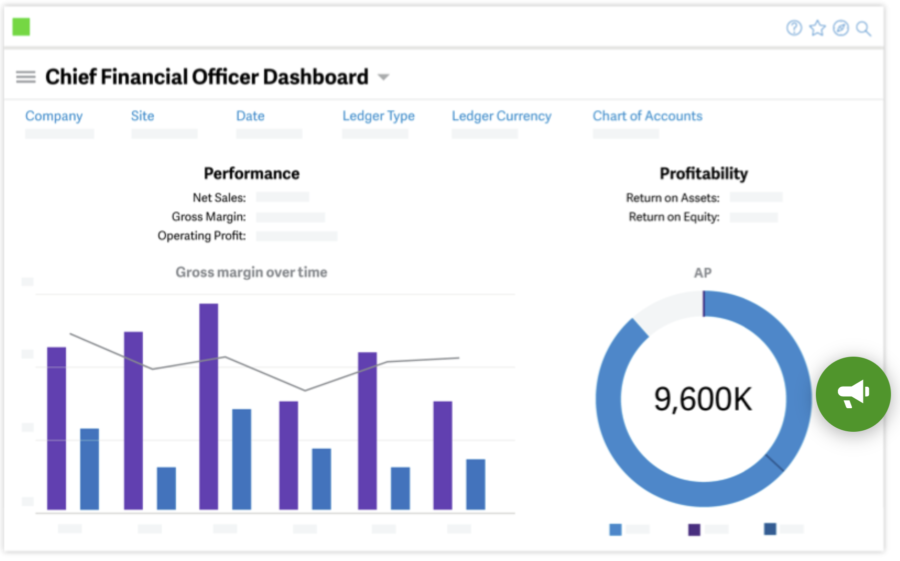
Many ERP users are not developers or technology experts, which makes it increasingly important for ERP software to be highly navigable and UI/UX-driven. Sage X3 receives high marks for its user-friendly interface, with many users noting its simple and streamlined dashboards.
Depending on the business operations segment you are looking at and your role in the operational infrastructure, your dashboards can be customized to the metrics you view most. You can easily navigate to other dashboards that aggregate related data in charts, graphs, and other visually driven analytics.
The dashboard interface is set up to aid in both navigation and self-service for troubleshooting, with guided prompts and a “Help” button found on every dashboard screen.
Scalability with Multiple Lines of Business
Sage X3 is built with scalability in mind, whether your business already includes several service lines or subsidiaries, or you plan to grow in the future.
The software allows you to separate your subsidiaries under one corporate umbrella into stock sites, financial sites, and other platforms. You can run them all as separate brands with separate goals while also splitting internal dashboards from customer-facing sites. However, these sites can still share relevant information back and forth — such as customer, supplier, and general ledger (G/L) data — for additional analytics capabilities.
Presented as a platform-agnostic tool, Sage X3 makes it easier for businesses to acquire companies with different business models and tech portfolios over time. The software is known for its high customization as well. Given the right plan and experts to carry it out, the tool can be built out and adjusted to meet the needs of different business lines.
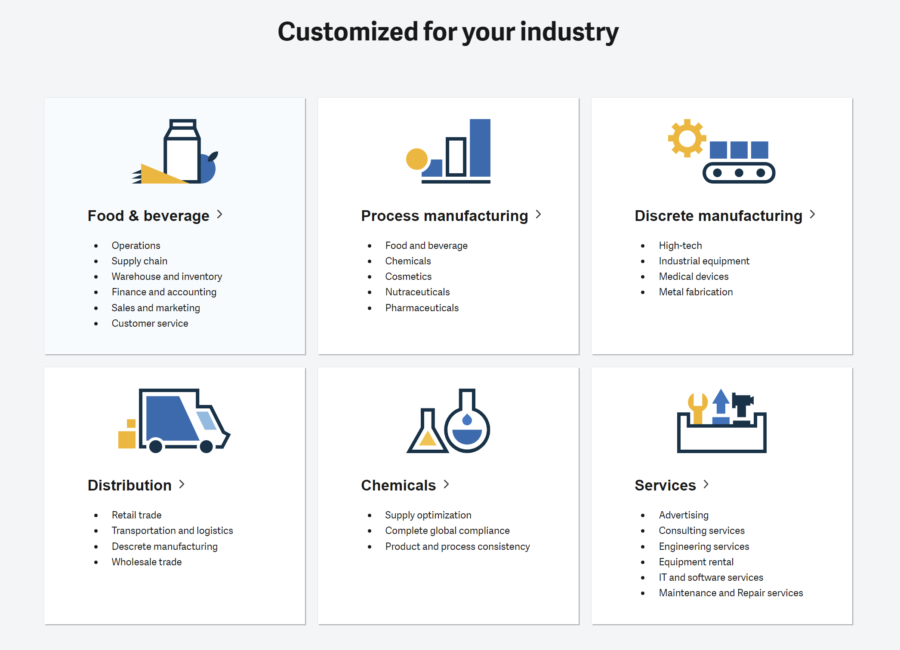
Sage X3 already includes industry-specific modules. If you work in these particular industries, no additional compliance measures or customizations need to be added to the tool:
- Food & beverage
- Process manufacturing (specifically for pharmaceuticals and cosmetics)
- Discrete manufacturing
- Distribution
- Chemicals
- Services
Fully Integrated and Automated Processes
Sage X3 offers fully integrated web services, which makes it possible to derive useful customer and process analytics from all websites and customer databases in a company’s portfolio. The focus on web integration also makes step-by-step process automation possible across business operations. Some examples of integration and automation in action include:
- Traceability for inventory, financial data, and manufacturing transactions across a product’s life cycle
- Order automation to the point of shipping and delivery
- Production management via bill of materials (BOM) planning, shop floor control, quality control, and project management features on X3 dashboards
The Cons of Sage X3 ERP
Difficulty of Custom Configurations
Although the tool is considered highly configurable, some users express frustration about how difficult it is to code custom configurations into the system. Out of 33 reviews on Gartner Peer Insights, approximately 28% of users comment on the difficulties of configuration and managing those configurations in Sage ERP software.
Some of the more specific configuration concerns from customers include the following:
- The difficulty of using and exporting Sage’s Crystal Reports leads many companies to do custom development for their reporting needs.
- Sage X3 focuses on six industry categories of operations, so many companies need to build custom tools for industries that go beyond those categories.
- Sage X3’s core language is a proprietary 4GL language. Few companies have the in-house experts to manage configurations in this language, leading them to seek out consultation and implementation from third-party vendors.
Concerns with Customer Support
With difficult customizations, some customers seek out strong customer support from Sage. However, user reviews have highlighted that the customer support offered by Sage is lacking in several key areas:
- Support tickets often go untouched by Sage experts for “days” and “weeks” at a time with no follow-up communication.
- Sage’s user community misses out on a forum approach for self-service and problem-solving.
- Sage customer service representatives often don’t have the technical, localized, or industry-specific expertise to provide the assistance customers need.
Because the customer service structure leaves some of Sage’s customers frustrated and lost in their configuration and implementation questions, they often hire third-party consultants to manage and troubleshoot within their systems.
Limited Quality Controls
With high levels of customization comes the potential for high levels of user error and diminished quality.
Some customers comment on the limited quality controls in Sage ERP software, noting that vague error message descriptions complicate the troubleshooting process and often lead to additional user errors down the road.
Other customers comment on how simple it is to change a code by clicking in the wrong section of the tool; they attribute this confusion and potential for error to the large number of X3 modules that overwhelm the average system user.
Selecting the Right ERP for Your Business
Sage X3 is a competitive solution in the ERP market, but that doesn’t mean it’s the best fit for your organization.
Dozens of ERP software and consulting firms offer a wide range of capabilities and pricing packages. Unless your team is well-versed in ERP implementation and your particular business strategy needs, it can feel challenging to select software that actually fits your goals.
Use the resources below to learn about other top players in the ERP space and how you can customize their platforms to work with your company’s existing business pain points.
Other Top ERP Tools to Consider
Oracle NetSuite ERP: The Pros and Cons
SAP ERP Software: S/4HANA Cloud Review for 2021
Industry-Specific Features to Consider
Key Features of Healthcare ERP Solutions
Essential Features in Foodservice ERP
Helpful Resources for ERP Selection
TechnologyAdvice’s ERP Software Selection Tool
The post Sage X3 ERP Software: The Pros & Cons for 2021 appeared first on CIO Insight.
topDaman News and Events
This showcases our company news and upcoming events. Please check back as this page will change frequently.


